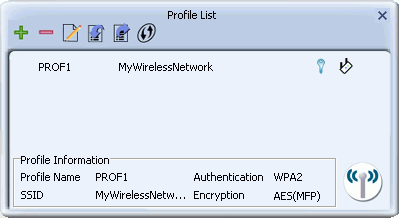
- For 'Profile Name', type a name for the profile, or leave at its default value.
- In the SSID field type the name of the network to which you are connecting, or select an existing network name from the drop-down list provided.
- For 'Network Type', select whether your network is an infrastructure or ad hoc network. If uncertain, leave at its default setting (Infrastructure).
-
- Select 'Infrastructure - Connect to AP' if you are connecting to a typical wireless network maintained by an AP or wireless router.
- Alternatively, select 'Ad Hoc - Connect to other computers' if you are connecting to a distributed network with no AP or router.
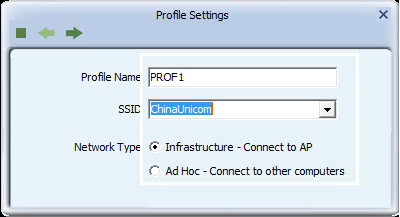
In the Profile Settings screen, click the right arrow to save your settings. For instructions on setting up a security method, click on the corresponding link.
- WAPI-CA
- CCKM, 802.1X, WPA or WPA2
-
Setting Up WAPI-CA
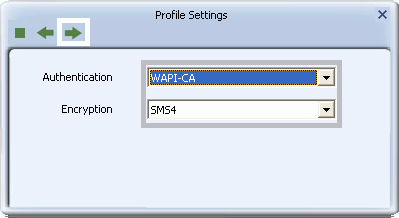
- To set up WAPI-CA security, for Authentication select WAPI-CA, and for Encryption select SMS4. Click the right arrow to save your settings.
- WAPI-CA requires user, issuer and authentication server unit (ASU) certificates. To install these certificates on your system, click the certificate installation button
 and follow the steps in the next screen. If these certificates are already installed on your system, skip the certificate installation procedure and go to the final step in these instructions on WAPI certificate installation.
and follow the steps in the next screen. If these certificates are already installed on your system, skip the certificate installation procedure and go to the final step in these instructions on WAPI certificate installation.
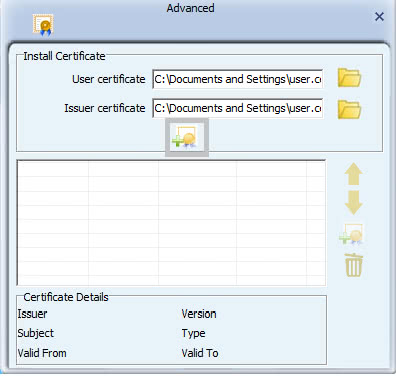
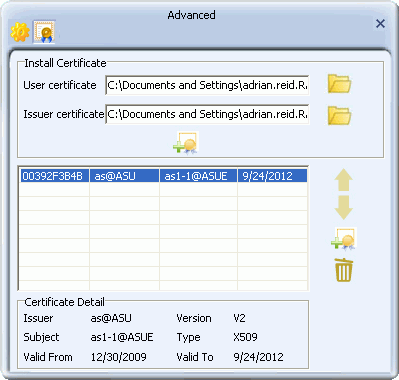
- To install WAPI certificates, first, in the certificate installation screen, in the 'User Certificate' field, click on the folder icon
 to browse to and select a WAPI user certificate. Then, in the 'Issuer Certificate' field, click on the folder icon
to browse to and select a WAPI user certificate. Then, in the 'Issuer Certificate' field, click on the folder icon  to browse to and select a WAPI issuer certificate. Next, click the first install button
to browse to and select a WAPI issuer certificate. Next, click the first install button  to verify the user and issuer certificate, and install the authentication server unit (ASU) certificate.
to verify the user and issuer certificate, and install the authentication server unit (ASU) certificate.
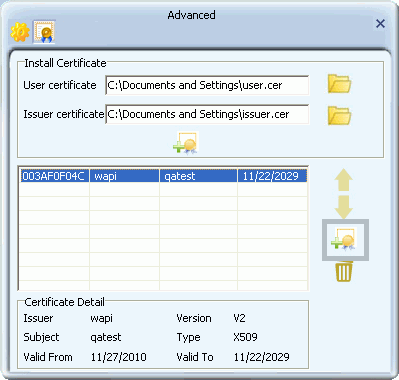
- The ASU certificate and its details appear in the screen.
- If the authentication server on your network is installed on your network's AP, you have completed certificate installation. Close this screen and go to the final step in this set of instructions.
- If the authentication server on your network is external to your network's AP, click the second install button to install the ASU.
-
- Click the 'Browse' button to browse to and select a ASU, and click 'Install'. The ASU appears in the list in this window. Click OK to close this screen.
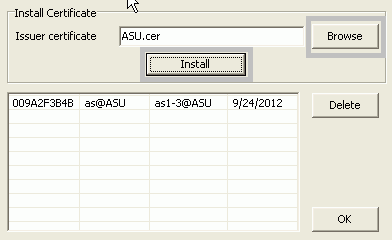
- The ASU appears in the certificate list. Close this window to complete the certificate installation procedure.
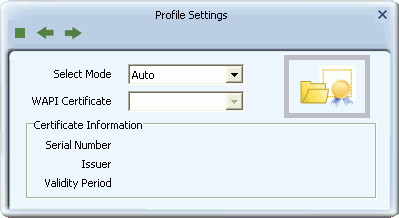
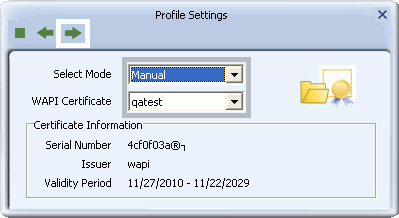
- Select 'Auto' to let the Utility automatically detect a valid certificate for your connection, or select 'Manual' and from the drop-down list, select the name of the certificate to be used in your connection. Click the right arrow to complete setting up WAPI-CA security.
Setting Up CCKM, 802.1X, WPA or WPA2
- In the Profile Settings security screen, select an authentication and encryption method.
- To set up WPA or WPA2 authentication, for Authentication select WPA or WPA2, and for Encryption select TKIP or AES. If WPA2 is selected, TKIP and AES are available with the added security of management frame protection (TKIP(MFP), AES(MFP)). Click the right arrow to save your settings.
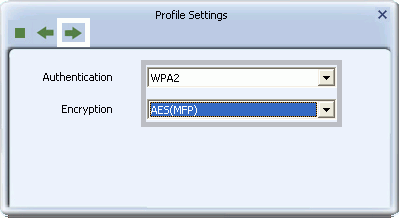
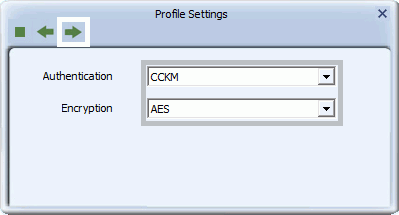
- To set up CCKM authentication, for Authentication select CCKM, and for Encryption select WEP, TKIP, or AES. Click the right arrow to save your settings.
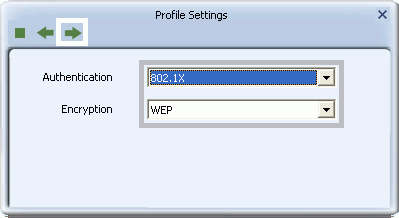
- To set up 802.1X authentication, for Authentication select 802.1X, and for Encryption select WEP. Click the right arrow to save your settings.
- To set up WPA or WPA2 authentication, for Authentication select WPA or WPA2, and for Encryption select TKIP or AES. If WPA2 is selected, TKIP and AES are available with the added security of management frame protection (TKIP(MFP), AES(MFP)). Click the right arrow to save your settings.
-
Select the EAP method (Extensible Authentication Protocol) supported by your network from the list below and follow the instructions given.
- PEAP
- TLS/Smart Card
- TTLS (Windows XP only)
- EAP-FAST
- MD5-Challenge (Windows XP, 802.1X only)
- LEAP
PEAP
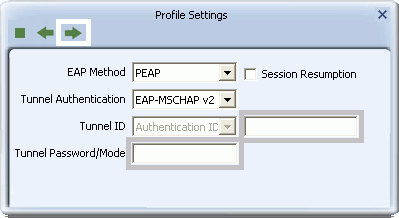
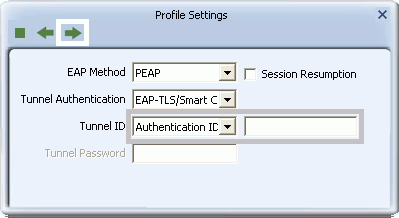
- If you select PEAP, for Tunnel Authentication select either EAP-MSCHAP v2, EAP-TLS/Smart Card, or Generic Token Card.
- If you select EAP-MSCHAP v2, in the Tunnel ID field type the name assigned to the user, and in the Tunnel Password field, type the password associated with the user name.
- If you select EAP-TLS/Smart Card, in the Tunnel ID field, select Authentication ID or Machine ID depending on whether user credentials are provided by a smart card or by the computer from which they are accessing the network. If Authentication ID is selected, in the adjacent field, type your user name.
- If you select Generic Token Card, in Tunnel Password/Mode, you can select Static Password or Soft Token and for Vista/Windows 7 users, Windows Logon or Prompt User, depending on the method used to supply user credentials.
- If you select the Static Password option, then in the Tunnel ID field, type your user name, and in the Tunnel Password field, type the password associated with your user name.
-
If you select Soft Token, your user credentials are supplied by software.
-
If you select Windows Logon, your user credentials are based on those of your Windows user account.
-
If you select Prompt User, when connecting to a network, a popup window appears, asking for your user name and password.
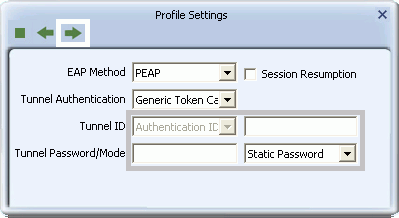
Click the right arrow to save your settings.
- If you select EAP-MSCHAP v2, in the Tunnel ID field type the name assigned to the user, and in the Tunnel Password field, type the password associated with the user name.
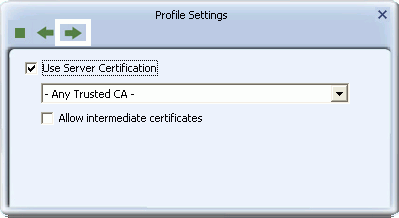
- If you have selected PEAP > EAP-MSCHAP v2 or PEAP > Generic Token Card, then optionally select Use Server Certification, and from the drop-down box, select the certificate authority. Click the right arrow to save your settings.
- If you have selected PEAP > EAP-TLS/Smart Card, from the drop-down list, select the client certificate on your computer to be used by this security method, or for Vista and Windows 7 users, select "Use my smart card" to set up smart card-based user authentication. Click the right arrow to save your settings.
- You have completed setup of PEAP authentication.
TLS/Smart Card
- If you select TLS/Smart Card, select Authentication ID or Machine ID depending on whether user credentials are provided by a smart card or by the computer from which they are accessing the network. If Authentication ID is selected, in the adjacent field, type your user name. Click the right arrow to save your settings.
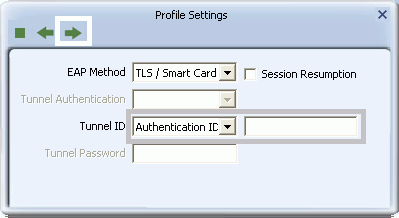
- From the drop-down list, select the client certificate on your computer to be used by this security method, or for Vista and Windows 7 users, select "Use my smart card" to set up smart card-based user authentication. Click the right arrow to save your settings.

-
Optionally select Use Server Certification, and from the drop-down box, select the certificate authority. Click the right arrow to save your settings.

- You have completed setup of TLS/Smart Card authentication.
TTLS
- For Windows XP users only. To apply TTLS, select a Tunnel Authentication method from the drop-down list. Options include CHAP, MS-CHAP, MS-CHAP v2, PAP, and EAP-MD5. For Tunnel ID, select Authentication ID or Machine ID depending on whether user credentials are provided by the user or by the computer from which they are accessing the network. If Authentication ID is selected, in the adjacent field, type your user name. For either Authentication ID or Machine ID, in the Tunnel Password field, type a password. Click the right arrow to save your settings.
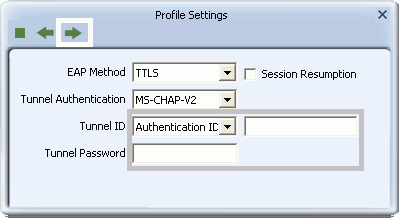
- From the drop-down list, optionally select the client certificate on your computer to be used by this security method, and click the right arrow to save your settings.
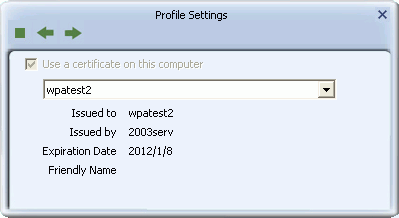
- Next, optionally select 'Use Server Certification'. From the drop-down box, select the certificate authority. Click the right arrow to save your settings.

-
You have completed setup of TTLS authentication.
EAP-FAST
- If you are applying EAP-FAST authentication using Vista or Windows 7, click the right arrow to finish setting up EAP-FAST.
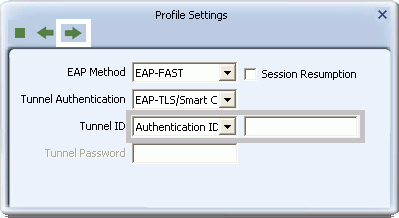
- Otherwise, for Windows XP users only, select a Tunnel Authentication method from the drop-down list. Options include EAP-MS-CHAP v2, EAP-TLS/Smart Card, and Generic Token Card.
- If you select EAP-MSCHAP v2, for 'Tunnel ID', select Authentication ID or Machine ID depending on whether user credentials are provided by users or by the computer from which they are accessing the network. If Authentication ID is selected, in the adjacent field, type your user name. If either Authentication ID or Machine ID are selected, for Tunnel Password, type the associated password.
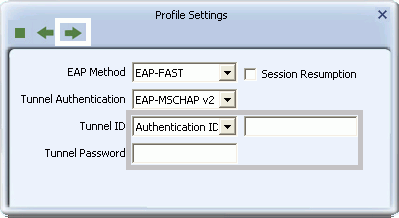
- If you select EAP-TLS/Smart Card, for 'Tunnel ID', select Authentication ID or Machine ID depending on whether user credentials are provided by a smart card or by the computer from which they are accessing the network. If Authentication ID is selected, in the adjacent field, type your user name.
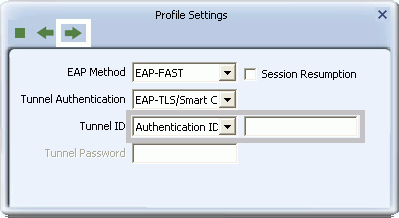
- If you select Generic Token Card, for 'Tunnel ID', field requirements depend on the tunnel mode and identification method selected.
- If 'Static Password' is selected for Tunnel Mode, and either Authentication ID or Machine ID are selected, type a password. For Authentication ID a user name is also required in the adjacent field.
- If 'Soft Token' is selected for Tunnel Mode, no further settings are required.
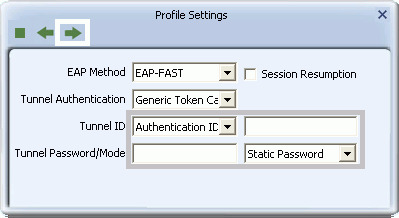
-
Click the right arrow to save your settings.
- If you select EAP-MSCHAP v2, for 'Tunnel ID', select Authentication ID or Machine ID depending on whether user credentials are provided by users or by the computer from which they are accessing the network. If Authentication ID is selected, in the adjacent field, type your user name. If either Authentication ID or Machine ID are selected, for Tunnel Password, type the associated password.
- For Windows XP users only, select 'Allow unauthenticated provision mode' to allow the allocation of PAC (protected authentication credentials) from the authentication server without authentication by users. Select 'Use protected authentication credential' to manually import a PAC. Click the right arrow to save your settings.
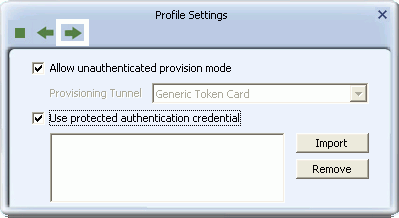
- For Windows XP users only, if you selected EAP-TLS/Smart Card as the tunnel authentication method, from the drop-down list select a security certificate on your computer. Click the right arrow to save your settings.

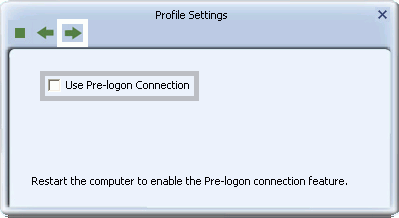
- For Windows XP, Vista and Windows 7, the Utility supports automatic login using your EAP-FAST settings on Windows startup. Select 'Use Pre-logon Connection' to enable this function. Click the right arrow to save your settings.
- You have completed setup of EAP-FAST authentication.
MD5-Challenge
- MD5-Challenge is available in Windows XP only. To apply MD5-Challenge, you need to have selected 802.1X as the security method. Type the Tunnel ID and Tunnel Password, and click the right arrow to save your settings.
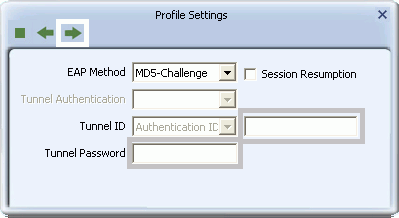
- In the screen that appears select a Key and Key Format setting supported by the wireless router or AP to which you are connecting.
- If you select 'Hex(10 or 26 hex digits)', in the WEP Key field type a security key 10 or 26 characters long made up of digits '0'-'9' and letters 'A'-'F'.
- If you select 'ASCII(5 or 13 ASCII characters)' in the WEP Key field, type a security key 5 or 13 characters long made up of digits '0'-'9' and letters 'a'-'z' and 'A'-'Z'.
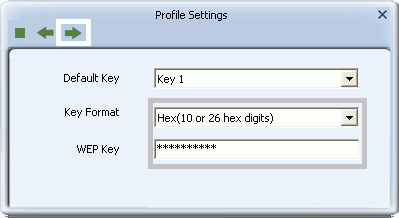
- Click the right arrow to save your settings and finish setting up MD5-Challenge authentication.
LEAP
- For Windows XP users, to apply LEAP, in the Tunnel ID field, select Authentication ID or Machine ID depending on whether user credentials are provided by users or by the computer from which they are accessing the network. If Authentication ID is selected, in the adjacent field, type the user name. For both Authentication ID and Machine ID, type a password for the user.
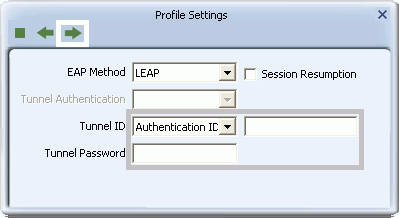
-
For Windows Vista and 7 users, for Tunnel Mode, you can select Static Password, Windows Logon or Prompt User, depending on the method used to supply user credentials.
- If you select the Static Password option, then in the Tunnel ID field, type your user name, and in the Tunnel Password field, type the password associated with your user name.
-
If you select Windows Logon, your user credentials are based on those of your Windows user account.
-
If you select Prompt User, when connecting to a network, a popup window appears, asking for your user name and password.
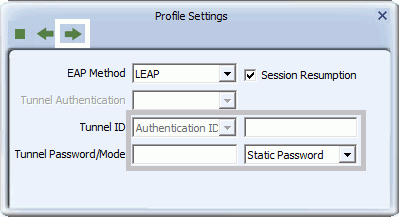
-
Click the right arrow to save your settings.
- The Utility supports automatic login using your LEAP settings on Windows startup. Select 'Use Pre-logon Connection' to enable this function. Click the right arrow to save your settings.

- You have completed setup of LEAP authentication.
- To set up WAPI-CA security, for Authentication select WAPI-CA, and for Encryption select SMS4. Click the right arrow to save your settings.