Niels Horn's Blog
Random thoughts, tips & tricks about Slackware-Linux, Lego and Star WarsUsing wireshark with remote capturing
February 6th, 2010 by Niels Horn in Monitoring, Slackware, networking
Wireshark is a very nice network protocol analyzer / sniffer, that is very complete and totally free and open source. It is the standard for examining network packets, used by many professionals and home users. I've been using wireshark since the days when it was still called Ethereal, some years ago.
The last few days I was struggling with the following situation:
- I wanted to examine some packets passing through my firewall
- my firewall is a "headless" (this means without a monitor, accessible only via ssh) Slackware server
- it has no X installed (and therefor no window manager etc.) so it won't run wireshark
Now wireshark can read packets captured by tcpdump and written to a file, so that's what I did at first:
- capture with tcpdump
- write the packets to a file on a network share
- open the file with wireshark
The problem is that I wanted to examine the packets "on-line", as they pass through the firewall.
Linux has a solution (inherited from Unix) for this, called "pipes". These are a special kind of files, where one program writes, while another reads from it, getting the contents in the right order.
In other words: the packet that went into the pipe first, will come out first at the other side of the pipe. Imagine it as a "vitrual tube".
It was a bit of a struggle to get all the parameters right, but in the end, I got it working like this (note: all commands are entered in a terminal session on the desktop):
- Create the pipe
niels@desktop:~$ mkfifo /tmp/pipes/cap_fw
"/tmp/pipes/" is where I create my pipes, feel free to use whatever directory you prefer.
"cap_fw" is the name of the pipe I selected. - Start tcpdump remotely with ssh from the desktop where you have wireshark installed:
niels@desktop:~$ ssh root@<firewall> "tcpdump -s 0 -U -n -w - -i eth1 not port 22" > /tmp/pipes/cap_fw
Replace <firewall> with the name or ip address of your remote server.The options I used are:
-s 0: use the required length to catch whole packets
-U: packet-buffering - write packet to pipe as soon as it is captured (as opposed to waiting for the buffer to fill)
-n: no address-to-name conversion (you can let wireshark do this if you want)
-w -: write output to standard output
-i eth1: capture from interface eth1 - change to match your setup
not port 22: leave out any packets from / to port 22. This is needed as we use ssh to connect to out firewall, so that we don't capture the captured packets again… If you need to examine port 22 on your server, use ssh over an alternative port.
> /tmp/pipes/cap_fw: redirect the output to our pipe. - While tcpdump is capturing packets and sending them to the pipe, open another terminal, start wireshark and use the pipe as the input
niels@desktop:~$ wireshark -k -i /tmp/pipes/cap_fw
Here the options mean:
-k: start immediately
-i /tmp/pipes/cap_fw: use our pipe as the "interface"
And you're up and running!
You can use all the normal functions of wireshark, like filtering, etc., as if you were capturing from a local interface.
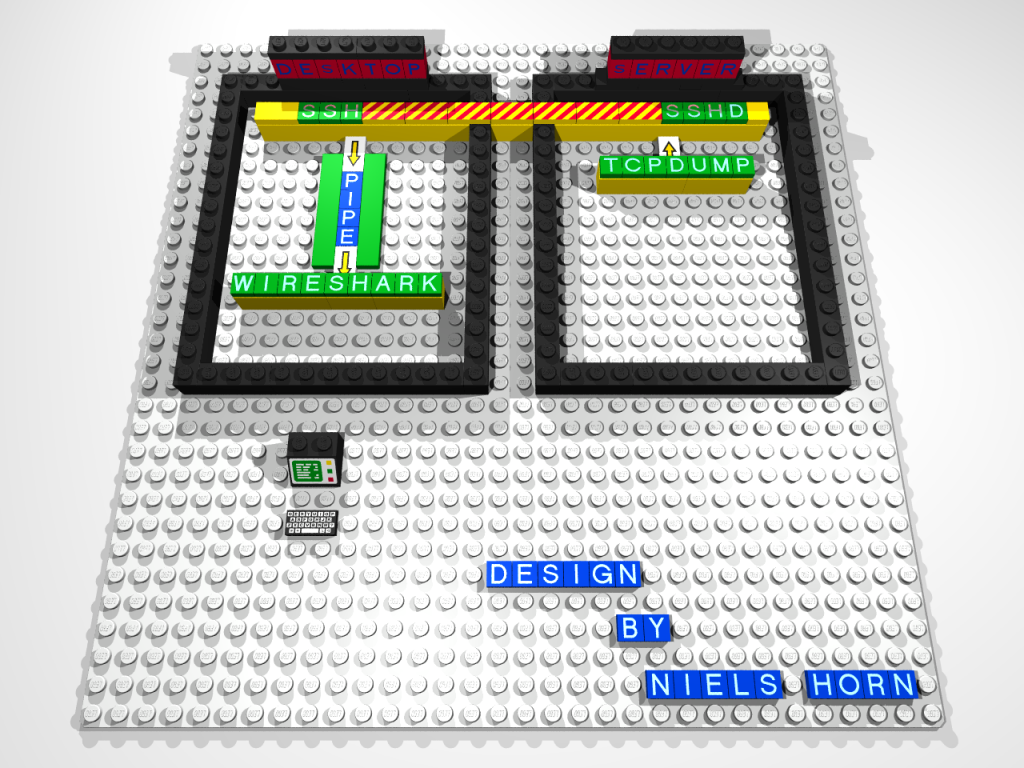
By special request from BP{k}, here is a diagram of the setup showing how ssh gets the data from the server, captured by tcpdump and sends it through the pipe to wireshark (with a little help from LeoCAD, l3p and POV-Ray):
(click on the image to enlarge it)
I might write a nice bash script to make things simpler now that I figured it all out.
If it is good enough in the end, I'll publish it here on my blog.