SELinux
SELinuxTraditional Linux security, called Discretionary Access Control (DAC), is based on users and groups. Because a process run by a user has access to anything the user has access to, fine-grained access control is difficult to achieve. Fine-grained access control is particularly important on servers, which often hold programs that require root privileges to run. SELinux (Security Enhanced Linux), developed by the U.S. National Security Agency (NSA), implements Mandatory Access Control (MAC) in the Linux kernel. MAC enforces security policies that limit what a user or program can do. It defines a security policy that controls some or all objects, such as files, devices, sockets, and ports, and some or all subjects, such as processes. Using SELinux, you can grant a process only those permissions it needs to be functional, following the principle of least privilege (page 392). MAC is an important tool for limiting security threats that come from user errors, software flaws, and malicious users. The kernel checks MAC rules after it checks DAC rules. SELinux can be in one of three states (modes):
Running SELinux in permissive or enforcing state degrades system performance between 5 and 10 percent. Although SELinux is usually of no benefit on a single-user system, you may want to consider SELinux for a server that connects to the Internet. If you are unsure whether to use SELinux, selecting permissive state allows you to change to disabled or enforcing state easily at a later date. SELinux implements one of the following policies:
This section discusses the targeted policy. With such a policy, daemons and system processes that do not have a specified policy are controlled by traditional Linux DACs. With the strict policy, all processes are controlled by SELinux (MACs). Setting up a system that runs under strict policy is beyond the scope of this book. There is always a tradeoff between security and usability. The targeted policy is less secure than the strict policy, but it is much easier to maintain. When you run the strict policy you will likely have to customize the policy so that users can do their work and the system can function as you would like it to. You can switch from one policy to the other (as explained shortly). However, it is not a good idea to switch from a targeted to a strict policy on a production system. If you do so, some users may not be able to do their work. You would need to customize the policy in such a case. Changing from a strict to a targeted policy should not create any problems. More InformationWeb
NSA: www.nsa.gov/selinux Centos Linux SELinux Wiki: fedoraproject.org/wiki/SELinux Centos Linux FAQ: fedora.redhat.com/docs/selinux-faq SELinux News: selinuxnews.org SELinux for Distributions (Sourceforge): selinux.sourceforge.net Unofficial FAQ: www.crypt.gen.nz/selinux/faq.html Centos Linux SELinux mailing list: www.redhat.com/mailman/listinfo/fedora-selinux-list Tip: Turning off SELinux There are two ways to disable SELinux. You can either modify the /etc/selinux/config file so that it includes the line SELINUX=disabled and reboot the system, or you can use system-configsecuritylevel (as explained on the next page). If there is a chance you will want to enable SELinux in the future, putting SELinux in permissive mode is a better choice than disabling it. This strategy allows you to turn on SELinux more quickly when you decide to do so.
config: The SELinux Configuration FileThe /etc/selinux/config file, which has a link at /etc/sysconfig/selinux, controls the state of SELinux on the local system. Although you can modify this file, it may be more straightforward to work with system-config-securitylevel (as explained in the next section). In the following example, the policy is set to targeted, but that setting is of no consequence because SELinux is disabled: $ cat /etc/selinux/config # This file controls the state of SELinux on the system. # SELINUX= can take one of these three values: # enforcing - SELinux security policy is enforced. # permissive - SELinux prints warnings instead of enforcing. # disabled - SELinux is fully disabled. SELINUX=disabled # SELINUXTYPE= type of policy in use. Possible values are: # targeted - Only targeted network daemons are protected. # strict - Full SELinux protection. SELINUXTYPE=targeted # SETLOCALDEFS= Check local definition changes SETLOCALDEFS=0 To put SELinux in enforcing mode, change the line containing the SELINUX assignment to SELINUX=enforcing. Similarly you can change the policy by setting SELINUXTYPE. Always set SETLOCALDEFS to 0. Tip: If you will use SELinux in the future If you will use SELinux in the future but not now, turn it on when you install Linux, and run it in permissive state with the policy set to the policy you will eventually use. Permissive state writes the required extended information to inodes, but it does not stop you from doing anything on the system. If you turn on SELinux after it has been disabled, when you reboot the system SELinux has to add extended attributes to the files in the filesystem. This process can take a long time on a large filesystem. If you are never going to use SELinux, disable it.
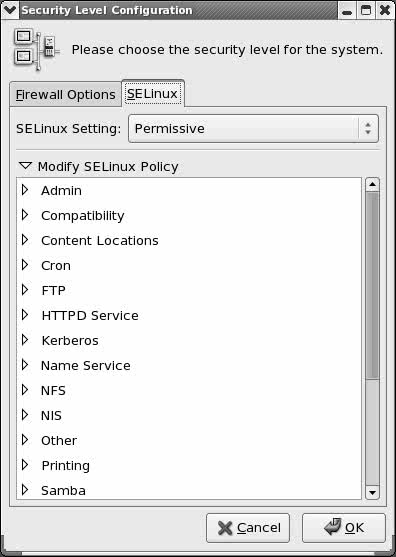
sestatus: Displays the State of SELinuxThe sestatus utility displays a summary of the state of SELinux on the local system: # sestatus SELinux status: enabled SELinuxfs mount: /selinux Current mode: permissive Mode from config file: permissive Policy version: 20 Policy from config file: targeted Setting the Targeted Policy with system-config-securitylevelThe system-config-securitylevel utility displays the Security Level Configuration window (Figure 11-1), which controls SELinux. To run this utility, enter system-configsecuritylevel from a command line in a graphical environment. From KDE select Main menu: Administration Figure 11-1. Security Level Configuration window, SELinux tab (system-config-securitylevel)
The lower frame, which occupies most of the Security Level Configuration window, holds the Modify SELinux Policy menu. You open and close a list of submenus or options by clicking the triangle adjacent to a submenu. Click the triangle next to Modify SELinux Policy to display a list of submenus. Some of these submenus are quite simple. For example, open the SpamAssassin (page 640) submenu to display the single choice: Allow Spam Assassin daemon network access. By default the targeted policy does not allow the SpamAssassin daemon, spamd, to access the network. Click the box next to this choice to display a check mark and allow network access for this daemon. The NFS submenu presents three choices concerning NFS filesystems. The SELinux Service Protection submenu allows you to disable SELinux protection for a long list of daemons. The targeted policy works with specific system services (daemons): crond, ftpd, httpd, named, NFS, NIS, CUPS, Samba, Spam Assassin, SQUID, and sshd. To change the SELinux policy for one of the services listed in the submenu, open that submenu and select from the choices. When you are finished making changes, click OK. |
Rescue Mode
|
 Security Level and Firewall or from GNOME select System: Administration
Security Level and Firewall or from GNOME select System: Administration