Password Security
Passwords are the primary method that Community Enterprise Linux uses to verify a user's identity. This is why password security is so important for protection of the user, the workstation, and the network.
For security purposes, the installation program configures the system to use Message-Digest Algorithm (MD5) and shadow passwords. It is highly recommended that you do not alter these settings.
If MD5 passwords are deselected during installation, the older Data Encryption Standard (DES) format is used. This format limits passwords to eight alphanumeric characters (disallowing punctuation and other special characters), and provides a modest 56-bit level of encryption.
If shadow passwords are deselected during installation, all passwords are stored as a one-way hash in the world-readable /etc/passwd file, which makes the system vulnerable to offline password cracking attacks. If an intruder can gain access to the machine as a regular user, they can copy the /etc/passwd file to their own machine and run any number of password cracking programs against it. If there is an insecure password in the file, it is only a matter of time before the password cracker discovers it.
Shadow passwords eliminate this type of attack by storing the password hashes in the file /etc/shadow, which is readable only by the root user.
This forces a potential attacker to attempt password cracking remotely by logging into a network service on the machine, such as SSH or FTP. This sort of brute-force attack is much slower and leaves an obvious trail as hundreds of failed login attempts are written to system files. Of course, if the cracker starts an attack in the middle of the night on a system with weak passwords, the cracker may have gained access before dawn and edited the log files to cover their tracks.
In addition to format and storage considerations is the issue of content. The single most important thing a user can do to protect their account against a password cracking attack is create a strong password.
When creating a secure password, it is a good idea to follow these guidelines:
Some insecure examples include the following:
Some insecure examples include the following:
Some insecure examples include the following:
Some insecure examples include the following:
Some insecure examples include the following:
Some insecure examples include the following:
The following guidelines will help you to create a strong password:
With all these rules, it may seem difficult to create a password that meets all of the criteria for good passwords while avoiding the traits of a bad one. Fortunately, there are some steps you can take to generate an easily-remembered, secure password. There are many methods that people use to create secure passwords. One of the more popular methods involves acronyms. For example:
"over the river and through the woods, to grandmother's house we go."
While creating secure passwords is imperative, managing them properly is also important, especially for system administrators within larger organizations. The following section details good practices for creating and managing user passwords within an organization. If an organization has a large number of users, the system administrators have two basic options available to force the use of good passwords. They can create passwords for the user, or they can let users create their own passwords, while verifying the passwords are of acceptable quality.
Creating the passwords for the users ensures that the passwords are good, but it becomes a daunting task as the organization grows. It also increases the risk of users writing their passwords down.
For these reasons, most system administrators prefer to have the users create their own passwords, but actively verify that the passwords are good and, in some cases, force users to change their passwords periodically through password aging. To protect the network from intrusion it is a good idea for system administrators to verify that the passwords used within an organization are strong ones. When users are asked to create or change passwords, they can use the command line application The password check that is performed at the time of their creation does not discover bad passwords as effectively as running a password cracking program against the passwords.
Many password cracking programs are available that run under Community Enterprise Linux, although none ship with the operating system. Below is a brief list of some of the more popular password cracking programs:
None of these tools are supplied with Community Enterprise Linux and are therefore not supported by CentOS, Inc. in any way.
Always get authorization in writing before attempting to crack passwords within an organization. Password aging is another technique used by system administrators to defend against bad passwords within an organization. Password aging means that after a specified period (usually 90 days), the user is prompted to create a new password. The theory behind this is that if a user is forced to change their password periodically, a cracked password is only useful to an intruder for a limited amount of time. The downside to password aging, however, is that users are more likely to write their passwords down.
There are two primary programs used to specify password aging under Community Enterprise Linux: the The In the above command, replace You can also use the The following is a sample interactive session using this command:
Refer to the man page for chage for more information on the available options.
You can also use the graphical User Manager application to create password aging policies, as follows. Note: you need Administrator privileges to perform this procedure.
Click the System menu on the Panel, point to and then click Users and Groups to display the User Manager. Alternatively, type the command Click the Users tab, and select the required user in the list of users.
Click Properties on the toolbar to display the User Properties dialog box (or choose Properties on the File menu).
Click the Password Info tab, and select the check box for Enable password expiration.
Enter the required value in the Days before change required field, and click OK.
Password Info pane illustration. For more information about user and group configuration (including instructions on forcing first time passwords), refer to Users and Groups.Creating Strong Passwords
Secure Password Creation Methodology
otrattw,tghwg.
7 for t and the at symbol (@) for a:
o7r@77w,7ghwg.
H.
o7r@77w,7gHwg.
Creating User Passwords Within an Organization
Forcing Strong Passwords
passwd, which is Pluggable Authentication Manager (PAM) aware and therefore checks to see if the password is too short or otherwise easy to crack. This check is performed using the pam_cracklib.so PAM module. Since PAM is customizable, it is possible to add more password integrity checkers, such as pam_passwdqc (available from http://www.openwall.com/passwdqc/) or to write a new module. For a list of available PAM modules, refer to http://www.kernel.org/pub/linux/libs/pam/modules.html. For more information about PAM, refer to "Pluggable Authentication Modules (PAM)".
Password Aging
chage command or the graphical User Manager (system-config-users) application.
-M option of the chage command specifies the maximum number of days the password is valid. For example, to set a user's password to expire in 90 days, use the following command:
chage -M 90 <username><username> with the name of the user. To disable password expiration, it is traditional to use a value of 99999 after the -M option (this equates to a little over 273 years).
chage command in interactive mode to modify multiple password aging and account details. Use the following command to enter interactive mode:
chage <username>~]#
chage davido
Changing the aging information for davido
Enter the new value, or press ENTER for the default
Minimum Password Age [0]: 10
Maximum Password Age [99999]: 90
Last Password Change (YYYY-MM-DD) [2006-08-18]:
Password Expiration Warning [7]:
Password Inactive [-1]:
Account Expiration Date (YYYY-MM-DD) [1969-12-31]:
~]#
system-config-users at a shell prompt.
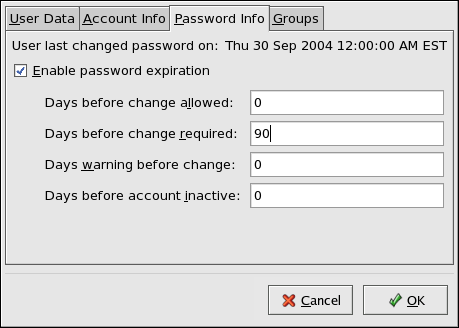
Figure 46.1. Specifying password aging options