PAM and Administrative Credential Caching
A number of graphical administrative tools in Community Enterprise Linux provide users with elevated privileges for up to five minutes using the pam_timestamp.so module. It is important to understand how this mechanism works, because a user who walks away from a terminal while pam_timestamp.so is in effect leaves the machine open to manipulation by anyone with physical access to the console.
In the PAM timestamp scheme, the graphical administrative application prompts the user for the root password when it is launched. When the user has been authenticated, the pam_timestamp.so module creates a timestamp file. By default, this is created in the /var/run/sudo/ directory. If the timestamp file already exists, graphical administrative programs do not prompt for a password. Instead, the pam_timestamp.so module freshens the timestamp file, reserving an extra five minutes of unchallenged administrative access for the user.
You can verify the actual state of the timestamp file by inspecting the /var/run/sudo/<user> file. For the desktop, the relevant file is unknown:root. If it is present and its timestamp is less than five minutes old, the credentials are valid.
The existence of the timestamp file is indicated by an authentication icon, which appears in the notification area of the panel.

Illustration of the authentication icon.
Figure 46.7. The Authentication Icon
Removing the Timestamp File
Before abandoning a console where a PAM timestamp is active, it is recommended that the timestamp file be destroyed. To do this from a graphical environment, click the authentication icon on the panel. This causes a dialog box to appear. Click the Forget Authorization button to destroy the active timestamp file.
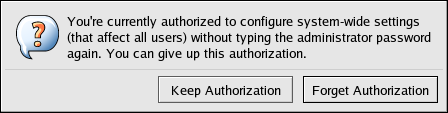
Illustration of the authentication dismissal dialog box.
Figure 46.8. Dismiss Authentication Dialog
You should be aware of the following with respect to the PAM timestamp file:
- If logged in to the system remotely using
ssh, use the/sbin/pam_timestamp_check -k rootcommand to destroy the timestamp file.
- You need to run the
/sbin/pam_timestamp_check -k rootcommand from the same terminal window from which you launched the privileged application. - You must be logged in as the user who originally invoked the
pam_timestamp.somodule in order to use the/sbin/pam_timestamp_check -kcommand. Do not log in as root to use this command. - If you want to kill the credentials on the desktop (without using the Forget Authorization action on the icon), use the following command:
pam_timestamp_check -k root </dev/null >/dev/null 2>/dev/nullFailure to use this command will only remove the credentials (if any) from the pty where you run the command.
Refer to the pam_timestamp_check man page for more information about destroying the timestamp file using pam_timestamp_check.
Common pam_timestamp Directives
The pam_timestamp.so module accepts several directives. The following are the two most commonly used options:
timestamp_timeout- Specifies the period (in seconds) for which the timestamp file is valid. The default value is 300 (five minutes).
timestampdir- Specifies the directory in which the timestamp file is stored. The default value is/var/run/sudo/.
Refer to "Installed Documentation" for more information about controlling the pam_timestamp.so module.