IPsec Host-to-Host Configuration
IPsec can be configured to connect one desktop or workstation (host) to another using a host-to-host connection. This type of connection uses the network to which each host is connected to create a secure tunnel between each host. The requirements of a host-to-host connection are minimal, as is the configuration of IPsec on each host. The hosts need only a dedicated connection to a carrier network (such as the Internet) and Community Enterprise Linux to create the IPsec connection.
A host-to-host IPsec connection is an encrypted connection between two systems, both running IPsec with the same authentication key. With the IPsec connection active, any network traffic between the two hosts is encrypted.
To configure a host-to-host IPsec connection, use the following steps for each host:
You should perform the following procedures on the actual machine that you are configuring. Avoid attempting to configure and establish IPsec connections remotely.
Select the type of encryption to use: manual or automatic.
If you select manual encryption, an encryption key must be provided later in the process. If you select automatic encryption, the Click Forward to continue.
To determine the IP address of the remote host, use the following command on the remote host:
where If only one Ethernet card exists in the system, the device name is typically eth0. The following example shows the relevant information from this command (note that this is an example output only):
The IP address is the number following the For host-to-host connections, both hosts should have a public, routable address. Alternatively, both hosts can have a private, non-routable address (for example, from the 10.x.x.x or 192.168.x.x ranges) as long as they are on the sam LAN.
If the hosts are on different LANs, or one has a public address while the other has a private address, refer to "IPsec Network-to-Network Configuration".
Click Forward to continue.
If manual encryption was selected in step 6, specify the encryption key to use, or click Generate to create one.
You may need to restart the network for the changes to take effect. To restart the network, use the following command:
After configuring the IPsec connection, it appears in the IPsec list as shown in Figure 46.10, "IPsec Connection".
IPsec Connection The following files are created when the IPsec connection is configured:
If automatic encryption is selected, When the interface is up, The first step in creating a connection is to gather system and network information from each workstation. For a host-to-host connection, you need the following:
For example, suppose Workstation A and Workstation B want to connect to each other through an IPsec tunnel. They want to connect using a pre-shared key with the value of You should choose a PSK that uses a mixture of upper- and lower-case characters, numbers and punctuation. An easily-guessable PSK constitutes a security risk.
It is not necessary to use the same connection name for each host. You should choose a name that is convenient and meaningful for your installation.
The following is the IPsec configuration file for Workstation A for a host-to-host IPsec connection with Workstation B. The unique name to identify the connection in this example is For Workstation A, The following is the content of the pre-shared key file (called To change the To change the authentication key at any time, edit the The next example shows the specific configuration for the phase 1 connection to the remote host. The file is called The default phase 1 configuration file that is created when an IPsec connection is initialized contains the following statements used by the Community Enterprise Linux implementation of IPsec:
Specifies that the subsequent stanzas of this configuration file apply only to the remote node identified by the The default configuration for IPsec on Community Enterprise Linux uses an aggressive authentication mode, which lowers the connection overhead while allowing configuration of several IPsec connections with multiple hosts.
Specifies the identification method to use when authenticating nodes. Community Enterprise Linux uses IP addresses to identify nodes.
Specifies the encryption cipher used during authentication. By default, Triple Data Encryption Standard (3DES) is used.
Specifies the hash algorithm used during phase 1 negotiation between nodes. By default, Secure Hash Algorithm version 1 is used.
Specifies the authentication method used during node negotiation. By default, Community Enterprise Linux uses pre-shared keys for authentication.
Specifies the Diffie-Hellman group number for establishing dynamically-generated session keys. By default, modp1024 (group 2) is used. The This default Denotes that SA can anonymously initialize with any peer provided that the IPsec credentials match. Defines the Diffie-Hellman key exchange protocol, which determines the method by which the IPsec nodes establish a mutual temporary session key for the second phase of IPsec connectivity. By default, the Community Enterprise Linux implementation of IPsec uses group 2 (or This parameter specifies the lifetime of an SA and can be quantified either by time or by bytes of data. The default Community Enterprise Linux implementation of IPsec specifies a one hour lifetime.
Specifies the supported encryption ciphers for phase 2. Community Enterprise Linux supports 3DES, 448-bit Blowfish, and Rijndael (the cipher used in the Advanced Encryption Standard, or AES).
Lists the supported hash algorithms for authentication. Supported modes are sha1 and md5 hashed message authentication codes (HMAC).
Defines the Deflate compression algorithm for IP Payload Compression (IPCOMP) support, which allows for potentially faster transmission of IP datagrams over slow connections. To start the connection, use the following command on each host:
where <nickname> is the name you specified for the IPsec connection.
To test the IPsec connection, run the Host-to-Host Connection
system-config-network to start the Network Administration Tool.
ipsec0. If required, select the check box to automatically activate the connection when the computer starts. Click Forward to continue.
racoon daemon manages the encryption key. The ipsec-tools package must be installed if you want to use automatic encryption.
ifconfig <device><device> is the Ethernet device that you want to use for the VPN connection.
eth0 Link encap:Ethernet HWaddr 00:0C:6E:E8:98:1D
inet addr:172.16.44.192 Bcast:172.16.45.255 Mask:255.255.254.0
inet addr: label.
service network restart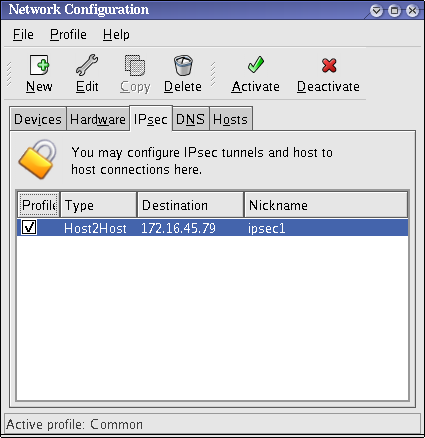
Figure 46.10. IPsec Connection
/etc/sysconfig/network-scripts/ifcfg-<nickname>/etc/sysconfig/network-scripts/keys-
<nickname>/etc/racoon/
<remote-ip>.conf/etc/racoon/psk.txt/etc/racoon/racoon.conf is also created.
/etc/racoon/racoon.conf is modified to include <remote-ip>.confManual IPsec Host-to-Host Configuration
ipsec1. This is used to identify the IPsec connection and to distinguish it from other devices or connections.
racoon.
Key_Value01, and the users agree to let racoon automatically generate and share an authentication key between each host. Both host users decide to name their connections ipsec1.
ipsec1, so the resulting file is called /etc/sysconfig/network-scripts/ifcfg-ipsec1.
DST=
X.X.X.X
TYPE=IPSEC
ONBOOT=no
IKE_METHOD=PSKX.X.X.X is the IP address of Workstation B. For Workstation B, X.X.X.X is the IP address of Workstation A. This connection is not set to initiate on boot-up (ONBOOT=no) and it uses the pre-shared key method of authentication (IKE_METHOD=PSK).
/etc/sysconfig/network-scripts/keys-ipsec1) that both workstations need to authenticate each other. The contents of this file should be identical on both workstations, and only the root user should be able to read or write this file.
IKE_PSK=Key_Value01
keys-ipsec1 file so that only the root user can read or edit the file, use the following command after creating the file:
chmod 600 /etc/sysconfig/network-scripts/keys-ipsec1keys-ipsec1 file on both workstations. Both authentication keys must be identical for proper connectivity.
X.X.X.X.confX.X.X.X is the IP address of the remote IPsec host. Note that this file is automatically generated when the IPsec tunnel is activated and should not be edited directly.
remote
X.X.X.X
{
exchange_mode aggressive, main;
my_identifier address;
proposal {
encryption_algorithm 3des;
hash_algorithm sha1;
authentication_method pre_shared_key;
dh_group 2 ;
}
}
X.X.X.X
X.X.X.X IP address.
The Racoon Configuration File
/etc/racoon/racoon.conf files should be identical on all IPsec nodes except for the include "/etc/racoon/ statement. This statement (and the file it references) is generated when the IPsec tunnel is activated. For Workstation A, the X.X.X.X.conf"X.X.X.X in the include statement is Workstation B's IP address. The opposite is true of Workstation B. The following shows a typical racoon.conf file when the IPsec connection is activated.
# Racoon IKE daemon configuration file.
# See 'man racoon.conf' for a description of the format and entries.
path include "/etc/racoon";
path pre_shared_key "/etc/racoon/psk.txt";
path certificate "/etc/racoon/certs";
sainfo anonymous
{
pfs_group 2;
lifetime time 1 hour ;
encryption_algorithm 3des, blowfish 448, rijndael ;
authentication_algorithm hmac_sha1, hmac_md5 ;
compression_algorithm deflate ;
}
include "/etc/racoon/X.X.X.X.conf";
racoon.conf file includes defined paths for IPsec configuration, pre-shared key files, and certificates. The fields in sainfo anonymous describe the phase 2 SA between the IPsec nodes - the nature of the IPsec connection (including the supported encryption algorithms used) and the method of exchanging keys. The following list defines the fields of phase 2:
modp1024) of the Diffie-Hellman cryptographic key exchange groups. Group 2 uses a 1024-bit modular exponentiation that prevents attackers from decrypting previous IPsec transmissions even if a private key is compromised.
ifup <nickname>tcpdump utility to view the network packets being transferred between the hosts and verify that they are encrypted via IPsec. The packet should include an AH header and should be shown as ESP packets. ESP means it is encrypted. For example:
~]#
tcpdump -n -i eth0 host <targetSystem>
IP 172.16.45.107 > 172.16.44.192: AH(spi=0x0954ccb6,seq=0xbb): ESP(spi=0x0c9f2164,seq=0xbb)