Digital Cryptography
Before we talk in detail about HTTPS, we need to provide a little background about the cryptographic encoding techniques used by SSL and HTTPS. In the next few sections, we'll give a speedy primer of the essentials of digital cryptography. If you already are familiar with the technology and terminology of digital cryptography, feel free to jump ahead to Section 14.7.
In this digital cryptography primer, we'll talk about:
Ciphers
Algorithms for encoding text to make it unreadable to voyeurs
Keys
Numeric parameters that change the behavior of ciphers
Symmetric-key cryptosystems
Algorithms that use the same key for encoding and decoding
Asymmetric-key cryptosystems
Algorithms that use different keys for encoding and decoding
Public-key cryptography
A system making it easy for millions of computers to send secret messages
Digital signatures
Checksums that verify that a message has not been forged or tampered with
Digital certificates
Identifying information, verified and signed by a trusted organization
The Art and Science of Secret Coding
Cryptography is the art and science of encoding and decoding messages. People have used cryptographic methods to send secret messages for thousands of years. However, cryptography can do more than just encrypt messages to prevent reading by nosy folks; it also can be used to prevent tampering with messages. Cryptography even can be used to prove that you indeed authored a message or transaction, just like your handwritten signature on a check or an embossed wax seal on an envelope.
Ciphers
Cryptography is based on secret codes called ciphers. A cipher is a coding scheme-a particular way to encode a message and an accompanying way to decode the secret later. The original message, before it is encoded, often is called plaintext or cleartext . The coded message, after the cipher is applied, often is called ciphertext . Screenshot 14-3 shows a simple example.

(Screenshot 14-3.)
Ciphers have been used to generate secret messages for thousands of years. Legend has it that Julius Caesar used a three-character rotation cipher, where each character in the message is replaced with a character three alphabetic positions forward. In our modern alphabet, "A" would be replaced by "D," "B" would be replaced by "E," and so on.
For example, in Screenshot 14-4, the message "meet me at the pier at midnight" encodes into the ciphertext "phhw ph dw wkh slhu dw plgqljkw" using the rot3 (rotate by 3 characters) cipher. The ciphertext can be decrypted back to the original plaintext message by applying the inverse coding, rotating -3 characters in the alphabet.
For simplicity of example, we aren't rotating punctuation or whitespace, but you could.

(Screenshot 14-4.)
Cipher Machines
Ciphers began as relatively simple algorithms, because human beings needed to do the encoding and decoding themselves. Because the ciphers were simple, people could work the codes using pencil and paper and code books. However, it also was possible for clever people to "crack" the codes fairly easily.
As technology advanced, people started making machines that could quickly and accurately encode and decode messages using much more complicated ciphers. Instead of just doing simple rotations, these cipher machines could substitute characters, transpose the order of characters, and slice and dice messages to make codes much harder to crack.
Perhaps the most famous mechanical code machine was the World War II German Enigma code machine. Despite the complexity of the Enigma cipher, Alan Turing and colleagues were able to crack the Enigma codes in the early 1940s, using the earliest digital computers.
Keyed Ciphers
Because code algorithms and machines could fall into enemy hands, most machines had dials that could be set to a large number of different values that changed how the cipher worked. Even if the machine was stolen, without the right dial settings (key values) the decoder wouldn't work.
In reality, having the logic of the machine in your possession can sometimes help you to crack the code, because the machine logic may point to patterns that you can exploit. Modern cryptographic algorithms usually are designed so that even if the algorithm is publicly known, it's difficult to come up with any patterns that will help evildoers crack the code. In fact, many of the strongest ciphers in common use have their source code available in the public domain, for all to see and study!
These cipher parameters were called keys. You needed to enter the right key into the cipher machine to get the decoding process to work correctly. Cipher keys make a single cipher machine act like a set of many virtual cipher machines, each of which behaves differently because they have different key values.
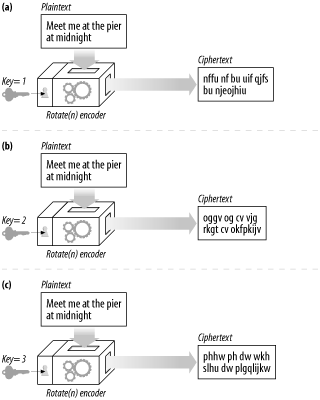
(Screenshot 14-5.)
Screenshot 14-5 illustrates an example of keyed ciphers. The cipher algorithm is the trivial "rotate-by-N" cipher. The value of N is controlled by the key. The same input message, "meet me at the pier at midnight," passed through the same encoding machine, generates different outputs depending on the value of the key. Today, virtually all cipher algorithms use keys.
Digital Ciphers
With the advent of digital computation, two major advances occurred:
· Complicated encoding and decoding algorithms became possible, freed from the speed and function limitations of mechanical machinery.
· It became possible to support very large keys, so that a single cipher algorithm could yield trillions of virtual cipher algorithms, each differing by the value of the key. The longer the key, the more combinations of encodings are possible, and the harder it is to crack the code by randomly guessing keys.
Unlike physical metal keys or dial settings in mechanical devices, digital keys are just numbers. These digital key values are inputs to the encoding and decoding algorithms. The coding algorithms are functions that take a chunk of data and encode/decode it based on the algorithm and the value of the key.
Given a plaintext message called P, an encoding function called E, and a digital encoding key called e, you can generate a coded ciphertext message C (Screenshot 14-6). You can decode the ciphertext C back into the original plaintext P by using the decoder function D and the decoding key d. Of course, the decoding and encoding functions are inverses of each other; the decoding of the encoding of P gives back the original message P.

(Screenshot 14-6.)